Flow Chart Of Cyber Security – Please click the following links to find flowcharts: The following slide presents a process flow which can be utilized for implementing business transformation and modernization. It involves relationship between technical actions coordinator, incident manager,. History, social & behavioral science humanity & fine art (hsbs/hfa) offered.
Keep in mind that the ffiec cat requirement for dfds falls into domain 4, which covers vendor management. This flowchart is provided as a. An incident management process flow chart is integral to understanding the sequence and interdependence of the steps to be followed in managing a cybersecurity incident. Why would the requirement for a dfd fall into the.
Flow Chart Of Cyber Security
Flow Chart Of Cyber Security
Ma 1160 or 1161 calc 1 (4 or. 5) semester 2 spring 15.5 credits. This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business.
This slide covers cyber security incident response process flowchart. Electrical & computer engineering 450 engineering. Much of it is discussions.
2020 cyber security curriculum undergrad flowchart 2020 cyber effective for all courses indicate hours have cs 300, cs security curriculum notes:
Strategic Cybersecurity Flowchart Download Scientific Diagram

Cyber Security Incident Response Process Flow Chart Deploying Computer
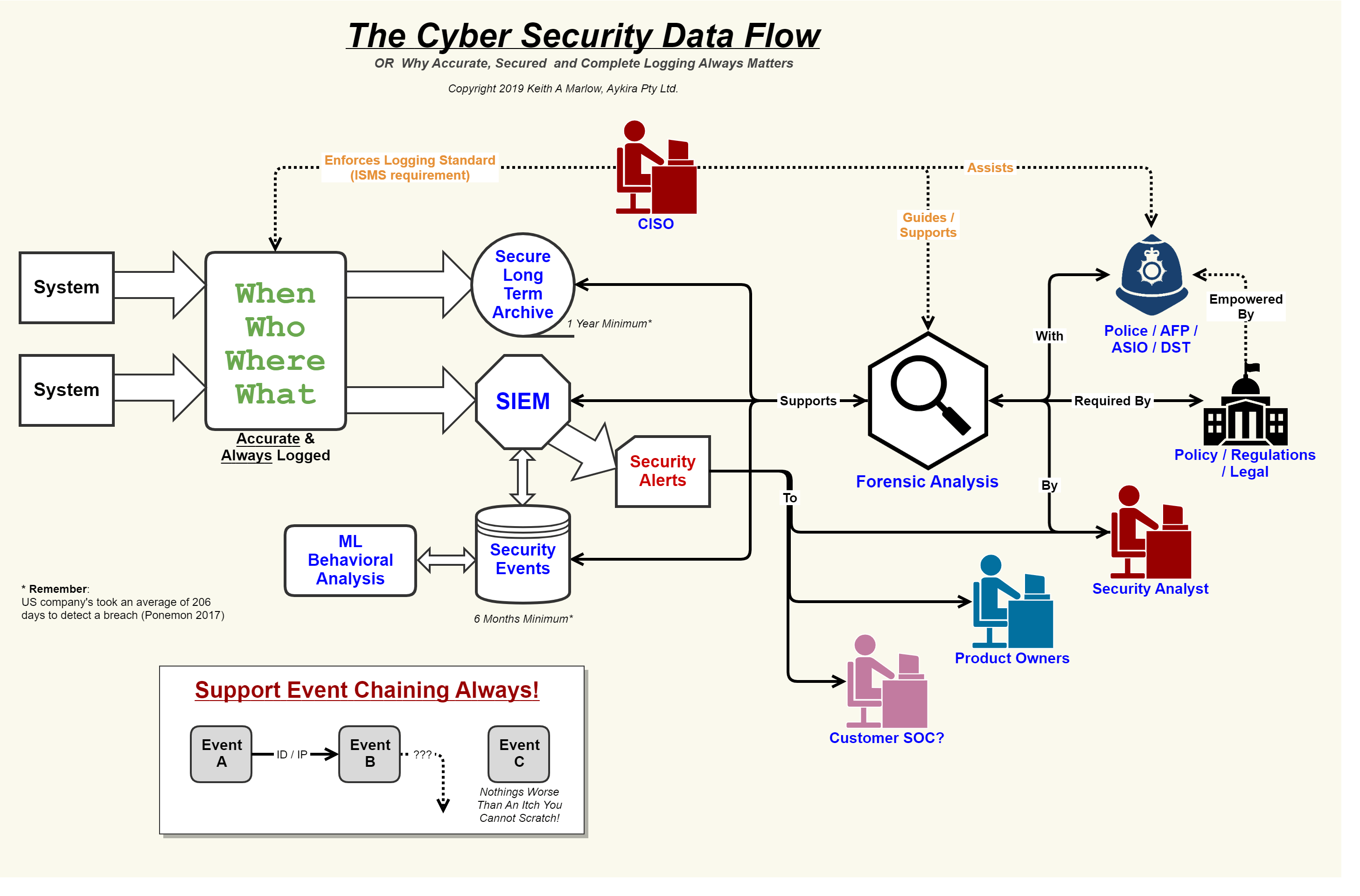
Security Event Logging, why it is so important Aykira Solutions

How to Create a Cybersecurity Crisis Management Plan in 5 Steps

Conducting Cybersecurity Risk Assessments Guide The Complete

Cybersecurity And Digital Business Risk Management Flow Diagram Of

NIST Cybersecurity Framework Process View Beşinci Güç Siber Güvenlik

Cyber Security Framework Mind Map Template

Cybersecurity Incident Response Plan Template and Example UK Cyber

Cyber Security Incident Response Process Flow Chart Ppt Powerpoint

Cyber Security Incident Response Process Flowchart

Cyber Security Isometric Flowchart Vector Illustration 2950850 Vector

Infographic Ten steps to cyber security SAFETY4SEA

Cyber Security Threat Assessment How to Manage Risk WBM Technologies
